攻击者正在利用你的Redis服务器吗?
月小升的博客用了redis加速,防止被攻击,直接把外部端口封死了,本地玩自己的。不过如果redis集群,那么必须开放端口了。好一点的做法是内网集群,只开放局域网IP端口,公网,太危险了。
今年早些时候,安全研究人员警告说,Apache Solr、Redis和Windows服务器可能受到加密器的攻击。
Imperva现在说,现在有太多面向互联网的Redis服务器,其中75%的服务器显示感染了恶意软件。
测试打开的Redis服务器
研究人员指出:“Redis是一个很好的工具,它可以作为内存中的分布式数据库、缓存或消息代理,并且非常流行。”
但是,Redis服务器的设计目的是让受信任的客户端在受信任的环境中访问,没有默认的身份验证,所有数据都以明文形式存储。
不幸的是,一个简单的Shodan搜索就会发现有72,000个公开可用的Redis服务器。
在建立自己的Redis服务器和他们开始探索(漏洞扫描)和受到攻击(简单的加密矿业感染和加密挖掘蠕虫)在一天内,研究人员决定看看有多少开放服务器运动恶意键和值,他们在redis数据库看到数据。
结果呢?只有10000个服务器对他们的扫描没有任何错误的回应,但是这些服务器中大多数显示出妥协的迹象。
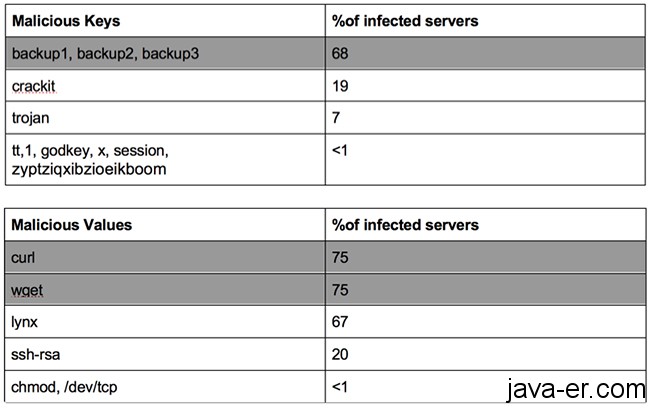
不出所料,超过三分之二的公开Redis服务器包含恶意密钥,四分之三的服务器包含恶意值,这表明服务器受到了感染。另外,根据我们的redis数据,被感染的带有“备份”密钥的服务器受到了一个位于中国的中型僵尸网络(占ip总数的86%)的攻击。
仅在上个月,Imperva的客户就被攻击了超过75k次,攻击者是295个运行Redis公共服务器的ip。这些攻击包括SQL注入、跨站点脚本编写、恶意文件上传、远程代码执行等。这些数字表明,攻击者正在利用易受攻击的Redis服务器对攻击者进行进一步攻击。
他们建议管理员从互联网上移除暴露的Redis服务器,并检查它们是否被感染。使用最少的权限运行Redis也是一个好主意。
原文
Are attackers harnessing your Redis server?
Earlier this year security researchers warned about vulnerable Apache Solr, Redis, and Windows servers hit with cryptominers.
Imperva now says that that are still too many Internet-facing Redis servers and that 75% of them show signs of having been infected with malware.
redis compromise
Testing open Redis servers
“Redis is a great tool, it can serve as in-memory distributed database, cache or a message broker and is widely popular,” the researchers note.
But Redis servers are designed to be accessed by trusted clients inside trusted environments, have not default authentication, and all the data is stored in clear text.
Unfortunately, a simple Shodan search shows that there are 72,000 publicly available ones.
And, after setting up their own honeypot Redis servers and them starting getting probed (vulnerability scans) and bombarded with attacks (simple crypto mining infections and crypto mining worms) within a day, the researchers decided to see how many of those open servers sport malicious keys and values that they saw in their honeypot data.
The result? Only 10,000 of the servers replied to their scan attempts without an error, but of those most showed signs of compromise.
Redis compromise
“Unsurprisingly, more than two-thirds of the open Redis servers contain malicious keys and three-quarters of the servers contain malicious values, suggesting that the server is infected. Also according to our honeypot data, the infected servers with ‘backup’ keys were attacked from a medium-sized botnet located at China (86% of IPs),” the researchers shared.
“In the last month alone, Imperva customers were attacked more than 75k times, by 295 IPs that run publicly available Redis servers. The attacks included SQL injection, cross-site scripting, malicious file uploads, remote code executions etc. These numbers suggest that attackers are harnessing vulnerable Redis servers to mount further attacks on the attacker’s behalf.”
They advise administrators to remove the exposed Redis servers from the Internet and check whether they have been infected. It’s also a good idea to run Redis with the minimal privileges necessary.
无特殊说明,文章均为月小升原创,欢迎转载,转载请注明本文地址,谢谢